Guide
This guide is gain access to a remote network or a remote service via a trusted host using the SSH protocol while ensuring encrypted traffic between the client and trusted host because the traffic is encrypted by the SSH tunnel, so all TCP communication are encrypted.
Prerequisites
- Two computers
- On a personal computer, install and configure a SSH server.
- On a company computer, install cygwin or Windows Subsystem Linux (WSL) to serve as your SSH client. Do note that WSL requires administrative privilege to install.
Anatomy of SSH
Secure Shell (SSH) provides remote shell connection via SSL encryption. A SSH tunnel is one way to setup a virtual private network (VPN) to encapsulate other layers of traffic that runs over TCP such as HTTP, RDP, SMTP, but SSH cannot forward UDP traffic such as DNS by itself.
There are numerous ways to setup such a connection, depending on the type of access and privilege you have on the computers.
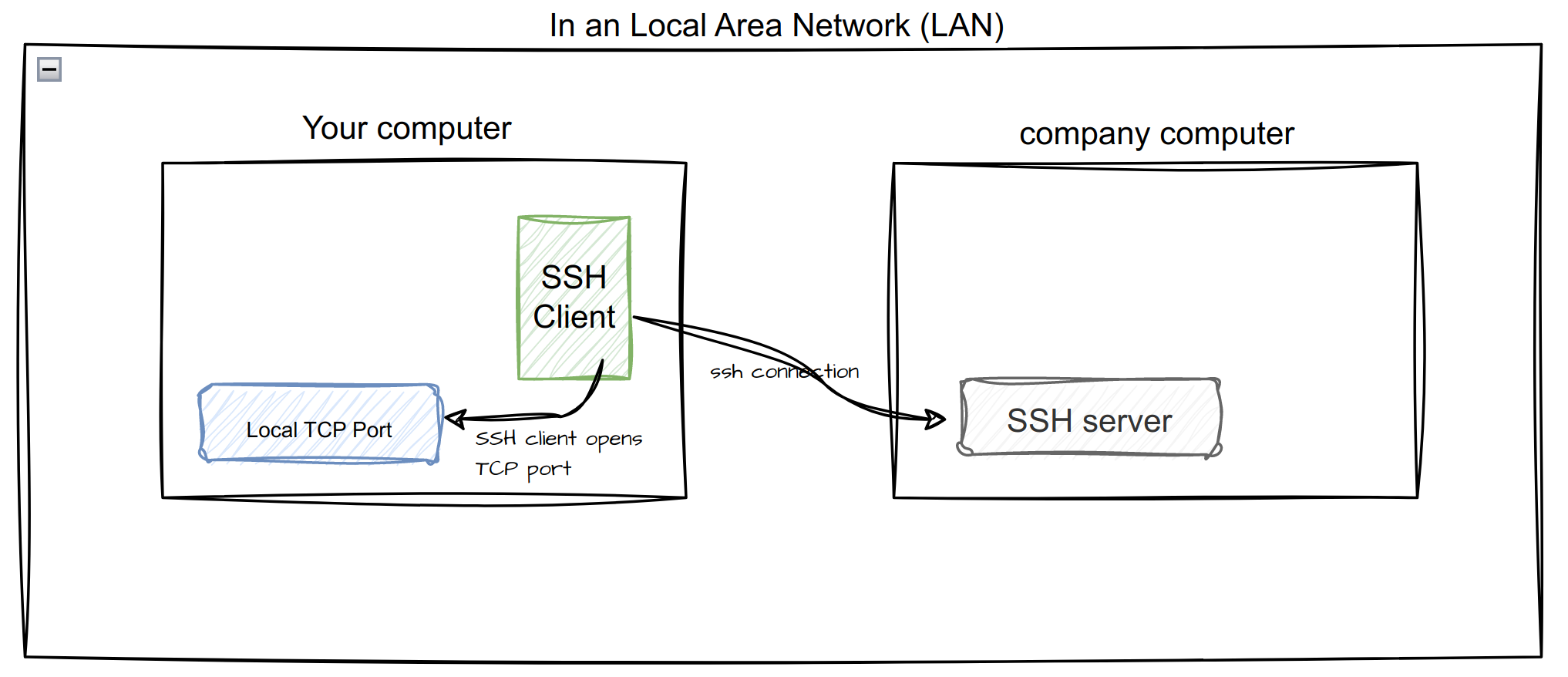
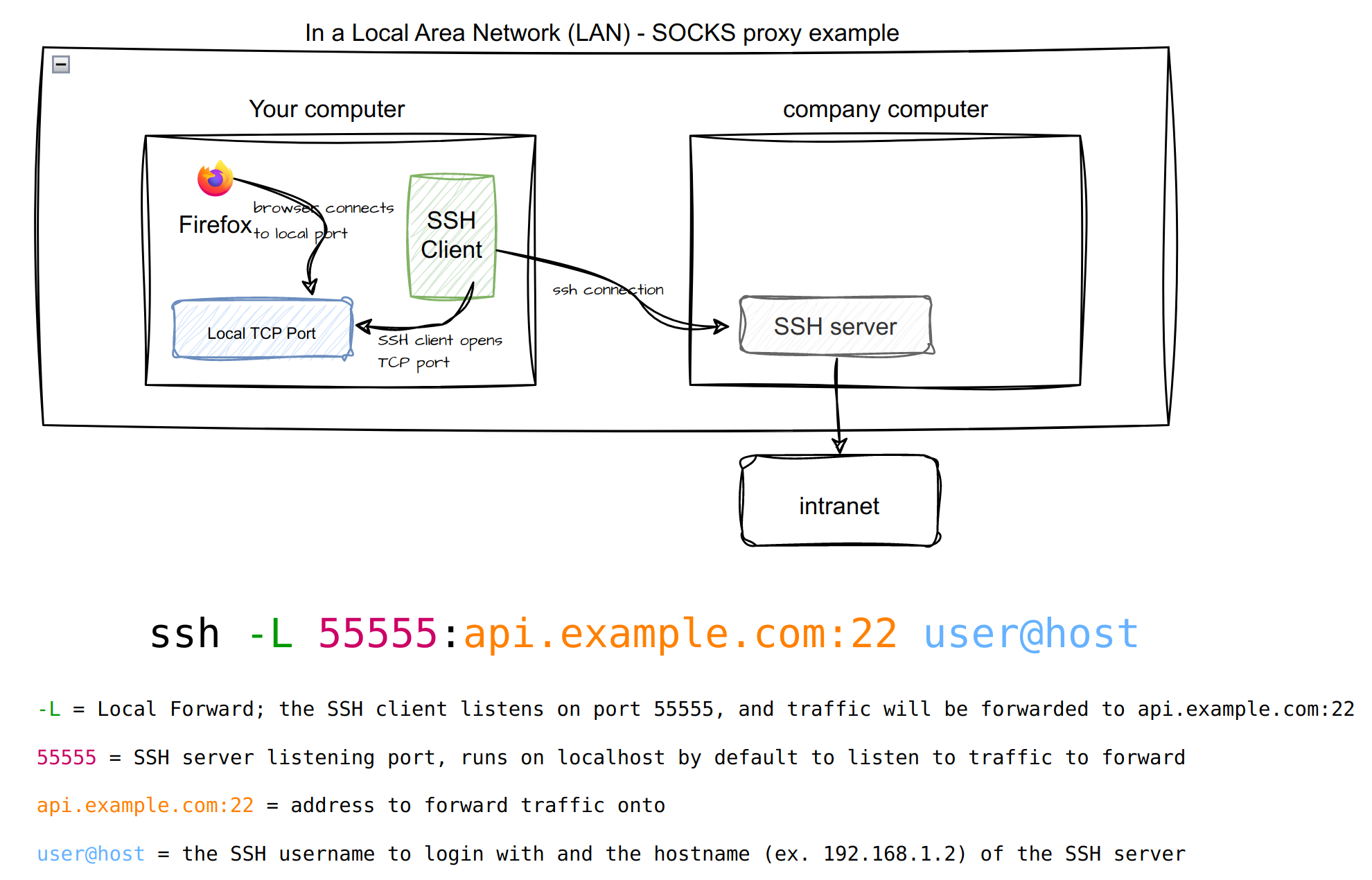
Local Forward Setup
This setup requires administrative rights and the ability to open up firewall rules on the company computer to allow inbound connections from SSH clients.
It generates process events when starting the SSH server, and when establishing a new SSH connection from a SSH client. This is not a preferred method of setting up a SSH connection.
To be able to browse the particular internal services (ex. MySQL, git, etc) via your local computer, an SSH connection is needed to route the traffic through.
- Setup the SSH server.
- Ensure the SSH server is listening on a particular port. This may require opening up any firewall or firewall protection. Follow examples from SSH Server - Ubuntu or SSH Server - Windows.
- Generate the SSH key pair on the SSH client.
- Provide the SSH server with the SSH client's public key.
- Start the SSH connection from the SSH client with a Local Forward command to proxy traffic to the particular endpoint.
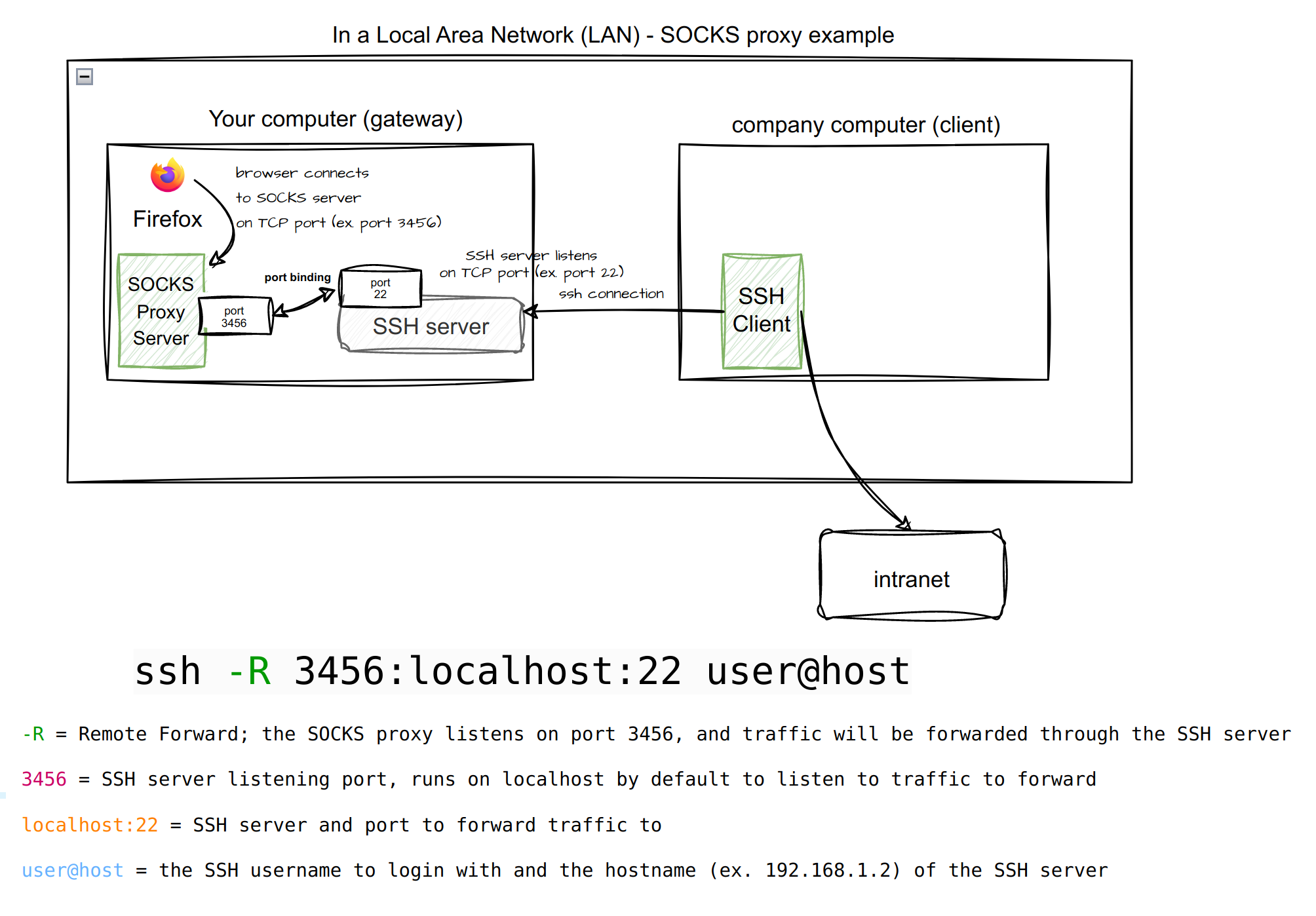
Remote Forward Setup
This setup provides a more hidden setup than the local forward setup. In many cases, depending on how locked down the company laptop is (ex. lack of admin privilege, lack of firewall permissions), this setup may be the only choice to be able to route traffic.
In this setup, the company laptop with access to the intranet will serve as a SSH client.
- Setup the SSH server on your own computer.
- Ensure the SSH server is listening on a particular port. This may require opening up any firewall or firewall protection. Follow examples from SSH Server - Ubuntu or SSH Server - Windows.
- Generate the SSH key pair on the SSH client.
- Provide the SSH server with the SSH client's public key.
- Start the SSH connection from the SSH client with a Remote Forward command to proxy traffic to the particular endpoint.
SOCKS5 Proxy
A SSH client can run as a SOCKS5 Proxy server that can do dynamic application level port forwarding, to tunnel browser traffic.
Using the -D will setup the SSH client as a SOCKS5 Proxy server. In this example below, traffic can be routed through your localhost (or 127.0.0.1) from port 3456 through the SSH tunnel to the SSH server listening on port 22.
You can now configure your browser to use the SOCKS5 proxy on localhost:3456 or use FoxyProxy browser plugin to dynamically control which URLs should go to the proxy and which ones should not.
Recommendation: change the default ssh port (22) to a higher numbered port. Preferrably a port higher than 2000 as all ports up to 2000 are privileged ports.
ssh -D 3456 -N -p 22 -vvv user@host
-D enables dynamic forwarding
22 is the port of localhost you are going to listen with proxy, this can be any port open of your computer
-N stops SSH from executing commands
-p is the port of the SSH server to connect to, in the above example, ensure port 22 is reachable from your client
-vvv is a verbose mode, and is useful when debugging various setup
The -f and -q command line argument can be used to fork SSH as a background process, and keep SSH quiet, instead of using -vvv as a verbose setup.
SSH Guides
These are additional articles with diagrams I've gone through to write this guide.