Proxy with SOCKS
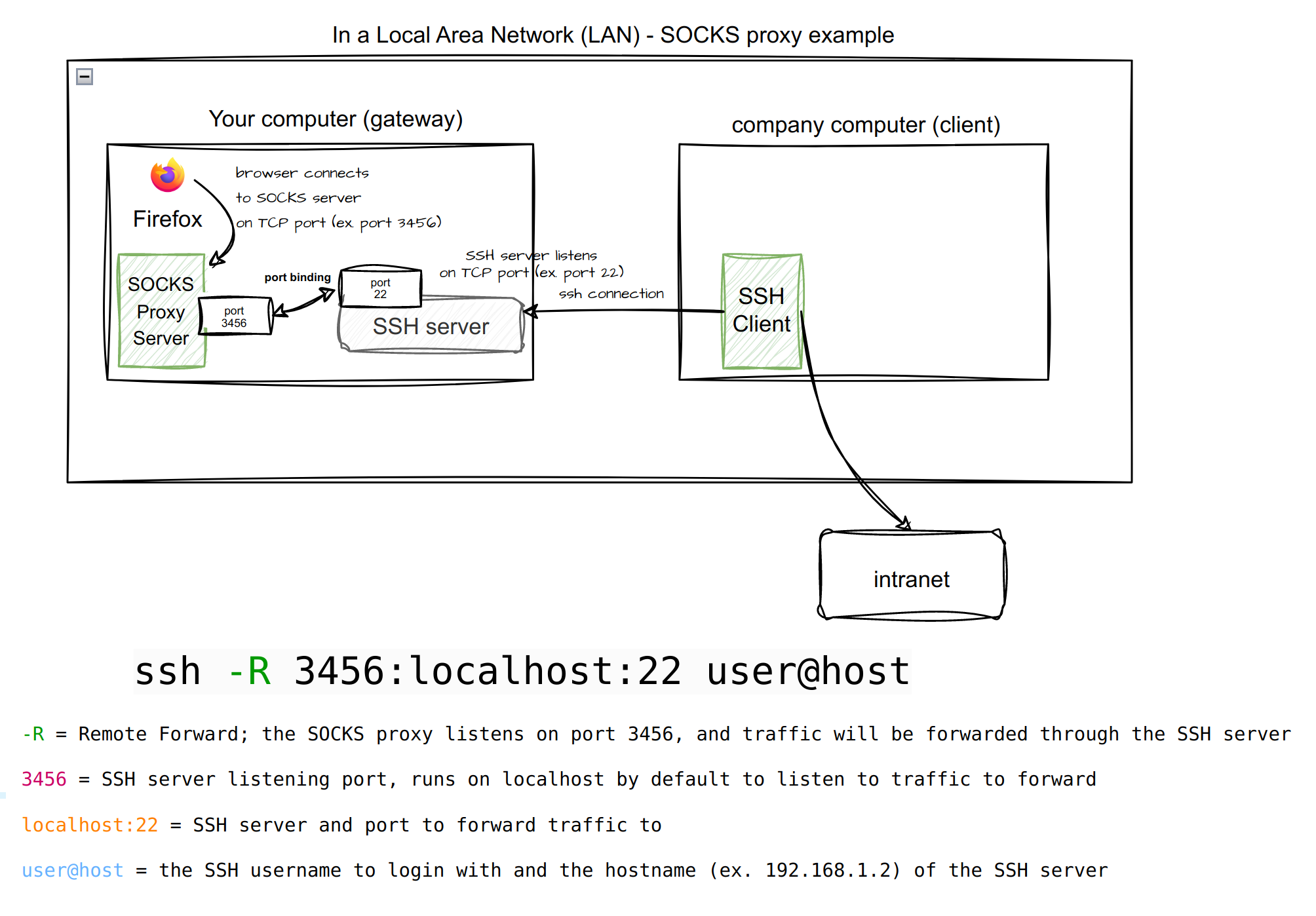
To proxy the traffic to the remote network using the SSH tunnel for web browsing, we have to setup a SOCKS5 session with local port forwarding.
In addition to the SOCKS proxy, we can rely on the SSH configuration and a browser plugin known as FoxyProxy to route traffic through the proxy when we need to via URL pattern matching.
SSH Configuration
The SSH configuration typically resides on a client machine's ~/.ssh/config file. A SSH configuration explains what SSH will do by default when it matches a particular Host in the configuration file.
For example, when running ssh example-network, SSH will try to connect to 192.168.0.1 on port 22 with the someusername and all the other configurations below.
The configuration uses RemoteForward, which specifies that a TCP port on the remote machine be forwarded over the secure channel to the specified host and port from the local machine. The configuration, when running on the SSH client, will mandate any traffic going through a particular local port on the SSH server to go through the SSH tunnel destinated to a particular host.
For traffic routed to the client machine's port 3456, it will be forwarded to port 22 where SSH will forward the connection to the destination websites determined by the client machine's SOCKS client (typically the web browser).
Host example-network
HostName 192.168.0.1
User someusername
PasswordAuthentication no
PubkeyAuthentication yes
IdentityFile ~/.ssh/example_network_id_ed25519
IdentitiesOnly yes
Port 22
ServerAliveInterval 10
ServerAliveCountMax 2
Compression yes
TCPKeepAlive yes
GatewayPorts yes
RemoteForward 3456
To complete the setup, run the SSH tunnel using one of these commands:
-N ensures SSH do not execute a remote command.
## For a verbose run - good for debugging purposes
## ctrl+c to kill the SSH tunnel/proxy.
ssh -vvvN example-network
## For quiet run
## ctrl+c to kill the SSH tunnel/proxy.
ssh -N example-network
## For background process run:
## To kill, ps -aux | grep ssh to find the process ID
## run kill -9 <pid>
ssh -fN example-network
## To check on status of the SSH tunnel:
## The output should have an entry for the network
ps aux | grep example-network | grep -v grep